A Tenchi Security está listada no Gartner® Market Guide for Third-Party Risk Management Technology Solutions*!
A Tenchi Security está listada no Gartner® Market Guide for Third-Party Risk Management Solutions!
Redução de Riscos Cibernéticos de Terceiros
Terceiros podem ampliar sua superfície de ataque e introduzir riscos incontroláveis à postura de segurança das organizações. Zanshin é a única solução global de TPCRM que combina visibilidade de dentro para fora (inside-out) e de fora para dentro (outside-in), unindo o monitoramento da superfície de ataque externa a avaliações automatizadas, contínuas, escaláveis e não intrusivas de infraestrutura de nuvem (IaaS, PaaS, SaaS) e controles de segurança - reduzindo de forma sistemática os riscos associados a todo o ecossistema de terceiros.

Terceiros podem agravar os riscos e expandir a superfície de ataque externa
Empresas dependem de seus parceiros de negócios para promover a inovação, aumentar a competitividade e reduzir custos. No entanto, a contratação de Terceiros pode, muitas vezes, ocorrer mais rapidamente do que a gestão dos riscos que eles podem introduzir.
Ecossistema de Ciberseguro
Entidades e serviços projetados para mitigar, transferir e gerenciar riscos cibernéticos.
Terceirização de processos empresariais
Empresas externas que gerenciam funções ou operações específicas em nome de uma organização.
Parceiros e afiliados
Indivíduos ou empresas que promovem seus produtos ou serviços em troca de uma comissão ou outro incentivo.
Fornecedores de API e processadores de pagamento
Serviços de Terceiros que possibilitam a troca de dados e transações financeiras entre diferentes sistemas de software.
Produtos SaaS missão-crítica
Soluções de software essenciais, baseadas em nuvem, das quais organizações dependem para suas principais operações comerciais.
Investimentos e Subsidiárias
Entidades nas quais sua organização possui participação financeira ou propriedade, compartilhando recursos e dados.
Serviços profissionais e de TI
Especialistas externos que oferecem conhecimento especializado e suporte técnico para complementar as capacidades internas.
Organizações Processadoras de Dados
Organizações que podem manipular, armazenar e/ou analisar dados em nome da sua empresa.
Precisamos tratar os Terceiros como o que realmente são: infraestruturas críticas para as organizações
As soluções oferecidas pelo mercado atualmente exigem que os Primeiros aceitem, reconheçam e transfiram riscos por meio de requisitos de conformidade e segurança. No entanto, isso não é suficiente, uma vez que os problemas de segurança de Terceiros podem se tornar questões críticas para todas as partes envolvidas.
Zanshin é a solução completa que efetivamente reduz os riscos cibernéticos de Terceiros
Zanshin é baseado em nossa metodologia para a Gestão de Riscos Cibernéticos de Terceiros. Acreditamos em uma relação mutuamente benéfica para todo o ecossistema, onde a gestão de riscos deve englobar remediação e mitigação, e não apenas a medição e aceitação.
Gestão do ciclo de vida completo, não apenas do pré-contrato
Monitoramento contínuo de fornecedores
Responsabilidade dos fornecedores com mecanismos de accountability
Colaboração com terceiros visando a obtenção de visibilidade e a redução
de riscos de maneira mutuamente benéfica
Remediação em primeiro lugar
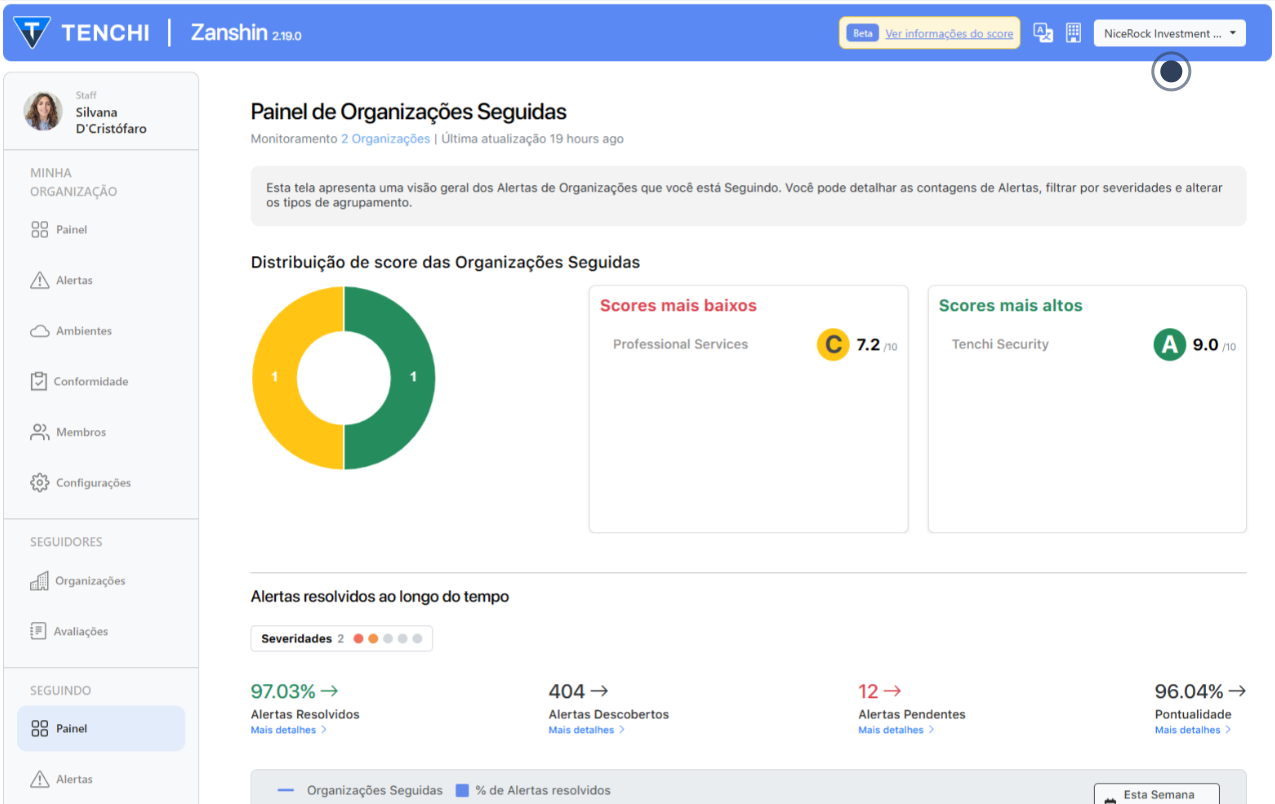
Tenha uma visão aprofundada da postura de segurança e da superfície externa de ataque de seus Terceiros
Integramos nossa solução de Gestão de Postura de Segurança de Terceiros aos seus parceiros e apresentamos os dados de risco necessários.

Visão Compartilhada, Responsabilidades Divididas
Zanshin capacita Primeiros a investir na melhoria da segurança de seus parceiros críticos. Ao invés de depender de varreduras externas, pontuações e auditorias anuais, nossa solução une ambas as partes (Primeiros e Terceiros) na redução de riscos.






O monitoramento contínuo assegura a responsabilização após a assinatura do contrato
Obtenha métricas sobre a pontualidade na correção e a disciplina de segurança de seus parceiros, e não apenas sua postura de segurança. Identifique quais deles têm desvios mais frequentes.

Acesso não intrusivo e indicadores de segurança confiáveis mantêm a abordagem amigável para Terceiros.
Colaboramos proativamente com parceiros e mantemos uma linha de comunicação aberta. Não introduzimos fontes de risco para essas partes.

Acreditamos que sua robustez e flexibilidade são diferenciais essenciais em um ambiente em constante mudança."


O dashboard é prático e facilita o acompanhamento, permitindo identificar eventuais brechas a cada inclusão ou alteração nos recursos. Nosso Motor de Pontos, que processa todos os programas de fidelidade dos cartões de crédito de um dos top 3 bancos do país, agora conta com Zanshin como pilar da nossa estratégia de segurança.
Recomendamos o Zanshin aos nossos clientes e prospects."
Estabeleça o novo padrão para a gestão de riscos cibernéticos de terceiros.
Terceiros e fornecedores externos podem ampliar suas superfícies de ataque e introduzir riscos incontroláveis à sua postura de segurança. O Zanshin é a única solução que reduz e gerencia sistematicamente os riscos associados a esse ecossistema.

Insights & Notícias



.svg)






